Cyber Security Management
Cyber Security Management
In order to undertake the Company's commitment to promoting the digital transformation of the industry, the sustainable development of the Group, the protection of employees' personal data and its trade secrets and reliable information and communication services, the cyber security management will be fully introduced to ensure the confidentiality, integrity and availability of information assets and the safety of information systems, equipment and networks. In addition, in order to ensure the rights and interests of our employees, customers and partners, to comply with the regulations of the Cyber Security Management Act and its sub-laws and to maintain a fair environment for market competition, we have hold an inter-departmental meeting to jointly formulate a report on cyber security management for the sustainable management of the enterprise as the top guideline for the Group's cyber security management.
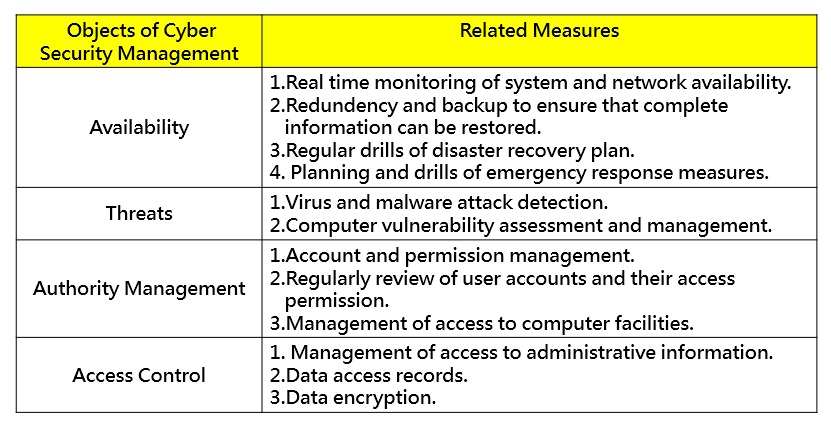
The objects of cyber security management are all employees in the Group, our customers, suppliers and shareholders, relevant trade secrets which include commercial trade secrets and technical trade secrets, and service providers and third-party personnel who have access to the Group's business information or provide services. In order to ensure the Company's cyber security, we have formulated relevant rules and guidelines by referring to proper technology and cyber security standards, and incorporated them into the system of corporate governance and operation management to protect the privacy and information security of employees, suppliers, partners and customers when conducting business contacts with each other.
The Company has passed the ISO27001 information security management system certification conducted by DQS on September 13, 2024, and obtained the certificate on October 29, 2024.

Cyber Security Risk Architecture
(1) The general manager of the Company convened to set up a cross-departmental cyber security committee, including the policy planning team who is responsible for leading and planning and under whose guidance all units cooperate with the implementation, the audit team who regularly reviews, tracks and audits the Group’s cyber security policies and plans and is responsible for supervising their implementation, and the emergency response team who is responsible for the emergency response of cyber security accidents and disasters. The committee is responsible for formulating cyber security management policies, regularly reviewing and revising them, holding regular meetings to review the implementation, and reporting the implementation and review to the board of directors on an annual basis to reduce cyber security risks.
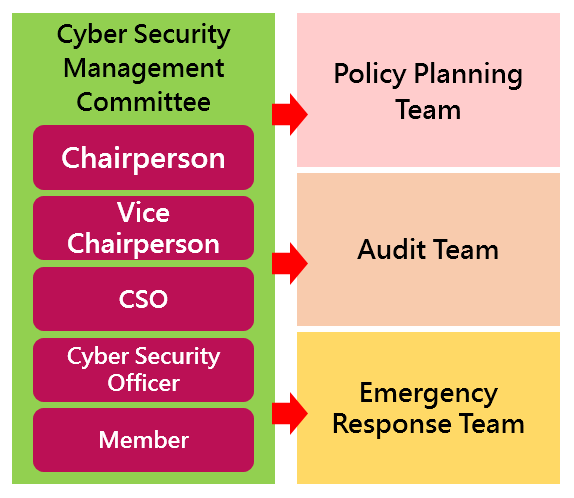
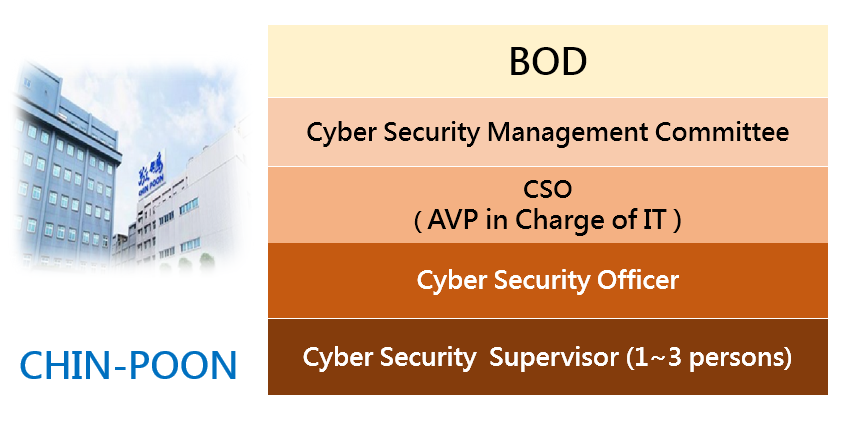
(2) The Information Department of the Group is the responsible office of cyber security, which is presided by chief security officer and administered by cyber security officer and several cyber security supervisors. The cyber security office is responsible for formulating the cyber security policies for the Group, planning and implementing cyber security management and its related policies, regularly issuing the Group's cyber security overview, and reporting on a regular basis to the Company's cyber security management committee.
Objectives of Cyber Security Policies
In order to ensure the continuous operation of the Company, the constant availability of the information communication services, the confidentiality, integrity and availability of the information assets and protection of the privacy of personnel data, we have established a sustainable operation plan for the information and communication services and meet the requirements of the information and communication services in accordance with the relevant laws and regulations. The policy planning goals are as follows:
(1) To optimize information system
To develop cyber security protection capabilities, to follow government policies and to enhance cyber security protection proficiency.
(2) To strengthen risk management
To ensure the integrity and availability of the Group's business information and to improve administrative efficiency and quality.
(3) To ensure information security
To ensure the confidentiality of information related to the Group's business and to protect the security of trade secrets and personal data.
(4) To improve customers satisfaction
To comply with laws and regulations of local governments and with internal regulations of the Group, to ensure the Group's cyber security and to achieve the Group’s goals of sustainable development.
Cyber Security Policies and their Review
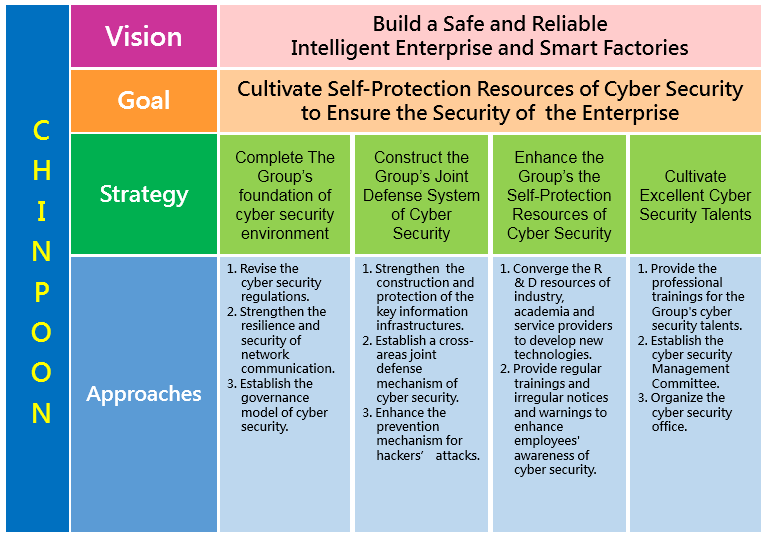
(1) The Group’s foundation of cyber security environment should be completed, relevant procedures should be established, and the revision of the internal cyber security regulations in the Group should be completed to ensure the confidentiality, integrity and availability of the information assets of the Group.
(2) We should strengthen the resilience and security of the Group’s foundation of communication network, implement various measures according to the architecture of cyber security responsibilities and establish the Group’s governance model of cyber security.
(3) We should construct the Group's joint defense system of cyber security, strengthen the construction and protection of the key information infrastructures and establish a cross-areas joint defense mechanism of cyber security. In addition to requiring our suppliers to comply with the relevant regulations of cyber security, we should conduct appropriate supervision and management of their subcontractors as well.
(4) We should enhance the prevention mechanism for hackers’ attacks, and establish a notification system for cyber security accidents and response mechanisms to ensure the proper response, control and handling of cyber security accidents.
(5) We should regularly perform cyber security audits, regularly survey the usage of all personnel and equipment within the cyber security management system and enhance the Group’s own resources to ensure the self-implementation of the cyber security management.
(6) We should provide regular education and trainings and give irregular cyber security notices or warnings to enhance employees' awareness of cyber security.
(7) We should establish the Group's cyber security office to provide the professional trainings for the cyber security talents for all units in the Group.
(8) The cyber security policies should be approved by the chief information officer, assessed at least once a year, and regularly reported to the cyber security management committee. If there are major changes in the organization (such as organizational architecture adjustments, major business changes, etc.), we should reassess the current cyber security policies and make corresponding revisions based on the reassessment results and the latest status of relevant regulations, technology, business and audit reports.
Approaches and Measures for Cyber Security Management
The Company is adopting the ISO 27001:2022 Information security, cybersecurity and privacy protection - Information security management systems in 2024.
(1) In accordance with the ISO 27001 requirements, we have implemented the "Plan-Do-Check-Act Cycle " (PDCA cycle) to establish operational procedures for cyber security management system. Various security measures can be divided into the following categories by using PDCA cycle.
a. Plan:
Establish policies and objectives for managing cyber security risks, formulate operational procedures for cyber security management system and assess the effectiveness of their management.
b. Do:
Regularly conduct management review and internal audit on the Group's cyber security policies, measure the effectiveness of the Group's cyber security operations and conduct risk analysis and assessment of the Group's cyber security.
c. Check:
Compare the difference between the results of the implementation and the expected targets and document usage records, track records and preserved evidence which are used as the necessary information in the cyber security audits
d. Act:
Propose a correction plan to reduce the difference between results and targets so that the next plan will be more complete to deal with cyber security. The corresponding actions facilitate the continuous correction and improvement of cyber security.
(2) Specific management projects for cyber security:
a. Comply with the laws and regulations and establish a compliance mechanism which completes the Group's internal regulations for cyber security and revises relevant operational procures to comply with the cyber security standards. And strengthen the resilience and security of the Group’s foundation of communication network.
b. Establish the Group’s governance model of cyber security, regularly reassess the current cyber security policies and make corresponding revisions based on the reassessment results and the latest status of relevant regulations, technology, business and audit reports.
c. Strengthen the construction and protection of the key information infrastructures and establish a cross-areas joint defense mechanism of cyber security. Our employees, our contractors and their subcontractors, depending on the business needs, should sign a Non-Disclosure Agreement (NDA) to ensure that those who use the Company's information to provide information services or perform related information services have the responsibility and obligation to protect the access to or the use of the Company’s information assets in order to protect from unauthorized access, modification, destruction or improper disclosure.
d. Identify the core business and the core systems of the Group, compile a list of information assets to establish a regular inventory of them, conduct risk management according to the risk assessment of cyber security and implement various control measures.
e. Enhance the prevention mechanism for hackers’ attacks, regularly perform redundancy and backup operations and regularly adjust and audit them.
f. Ensure the processes of core business (key system) are not affected by major failures and disasters, formulate contingency plans, establish appropriate redundancy or monitoring mechanisms and conduct regular drills to ensure that operational processes are recovered in time and maintain their availability.
g. Install antivirus software on the computers of the Company and prohibit the use of unauthorized software. The account number, password and permission of our employees should be properly kept and used and changed on a regular basis.
h. Formulate the standard procedures for responding to and reporting cyber security accidents so as to appropriately deal with them in a timely manner to avoid the spillage of their damage.
i. All employees should abide by legal regulations and the requirements of the cyber security policies. And the supervisors should supervise the implementation of the cyber security system and enhance employees' awareness of cyber security and legal compliance.
j. Converge the R & D resources of industry, academia and service providers to develop new technologies, provide regular education and trainings and give irregular cyber security notices or warnings to enhance employees' awareness of cyber security.
(3) Information Security Notification Procedure
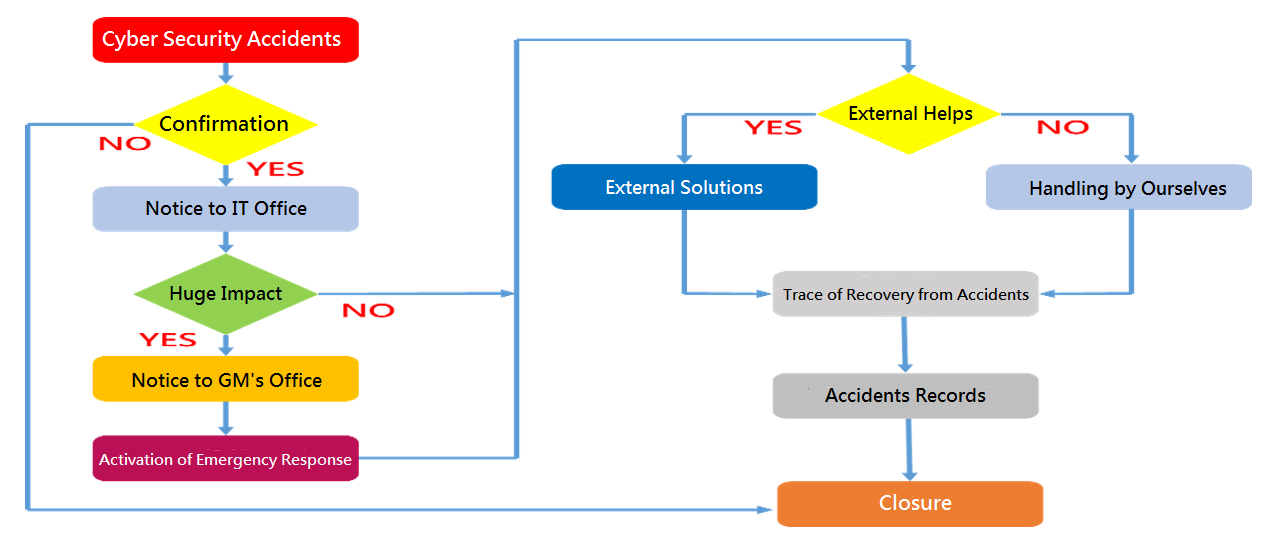
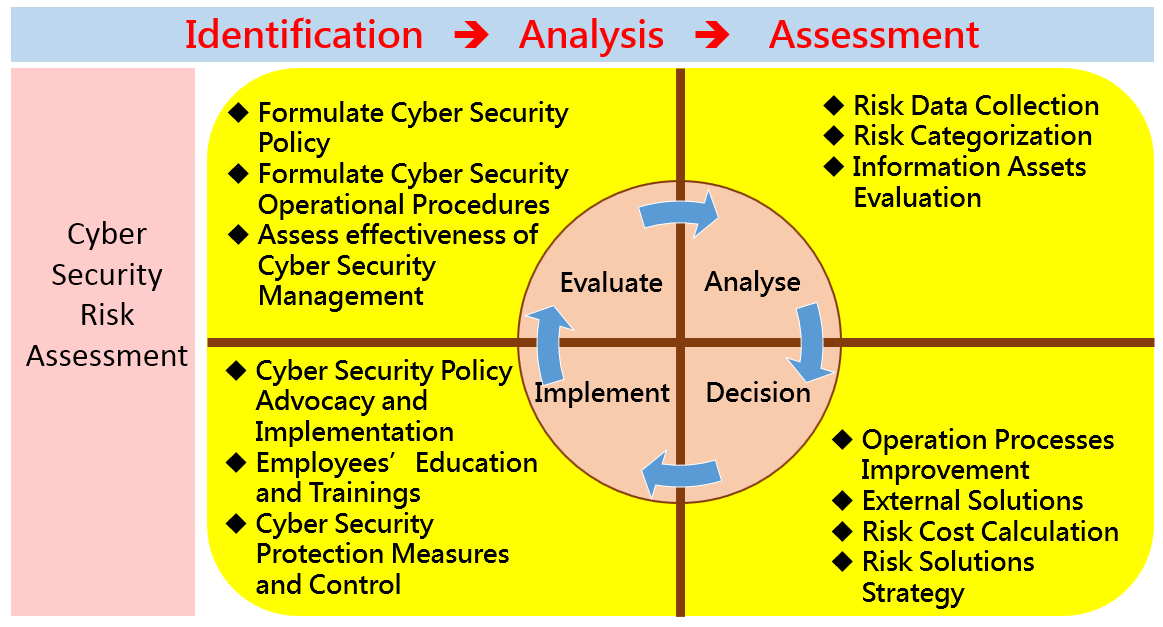
(4) Cyber Security Risk Assessment
a. The Group allocates limited resources to control cyber security according to the various levels of risk. Through control measures, we manage to reduce the Group's cyber security risk to an acceptable level. We systematically manage the risk of the Group's cyber security and effectively protect the investment in the Group's information and communication resources.
b. The Information Department of the Group is the responsible office of cyber security, which is administered by cyber security officer and several cyber security supervisors. The cyber security office is responsible for formulating the cyber security policies for the Group, planning and implementing cyber security management and its related policies, regularly reporting to the board of directors on its cyber security management overview, and regularly issuing the overview in order to facilitate the Group’s sustainable development.
c. The Group establishes a cyber security audit team through the cyber security management committee, which is responsible for supervising and auditing the implementation of cyber security management within the Group. If there is any defect found in the audit, it will immediately ask the audited unit to propose relevant correction plans and specific actions and regularly track their corrections to effectively reduce internal cyber security risks.
d. We conduct continuous audit and improvement through PDCA cycle to ensure the achievement of the Group's goals of reliability and continuous improvement
Implementation of Cyber Security Advocacy in 2023
- We have conducted two batches of cyber security education, totaling 6 hours.
- We have conducted three batches of "Simulation Training on Social Engineering" with a total of 600 managers and employees attending.
Cyber Security Management Implementation in 2023
- Cyber security accidents: The Company had no material cyber security incident in 2023.
- Drills on cyber security accidents and awareness notice: We have conducted two drill on recovery from redundancy in case of accidents, three drills on social engineering and four emergency response drills. We also gave awareness notice on cyber security to all employees on a quarterly basis and reported the status and major issues of cyber security in the top management committee once per month. All is to enhance the officers’ and all employees' response and awareness against cyber security risks.
